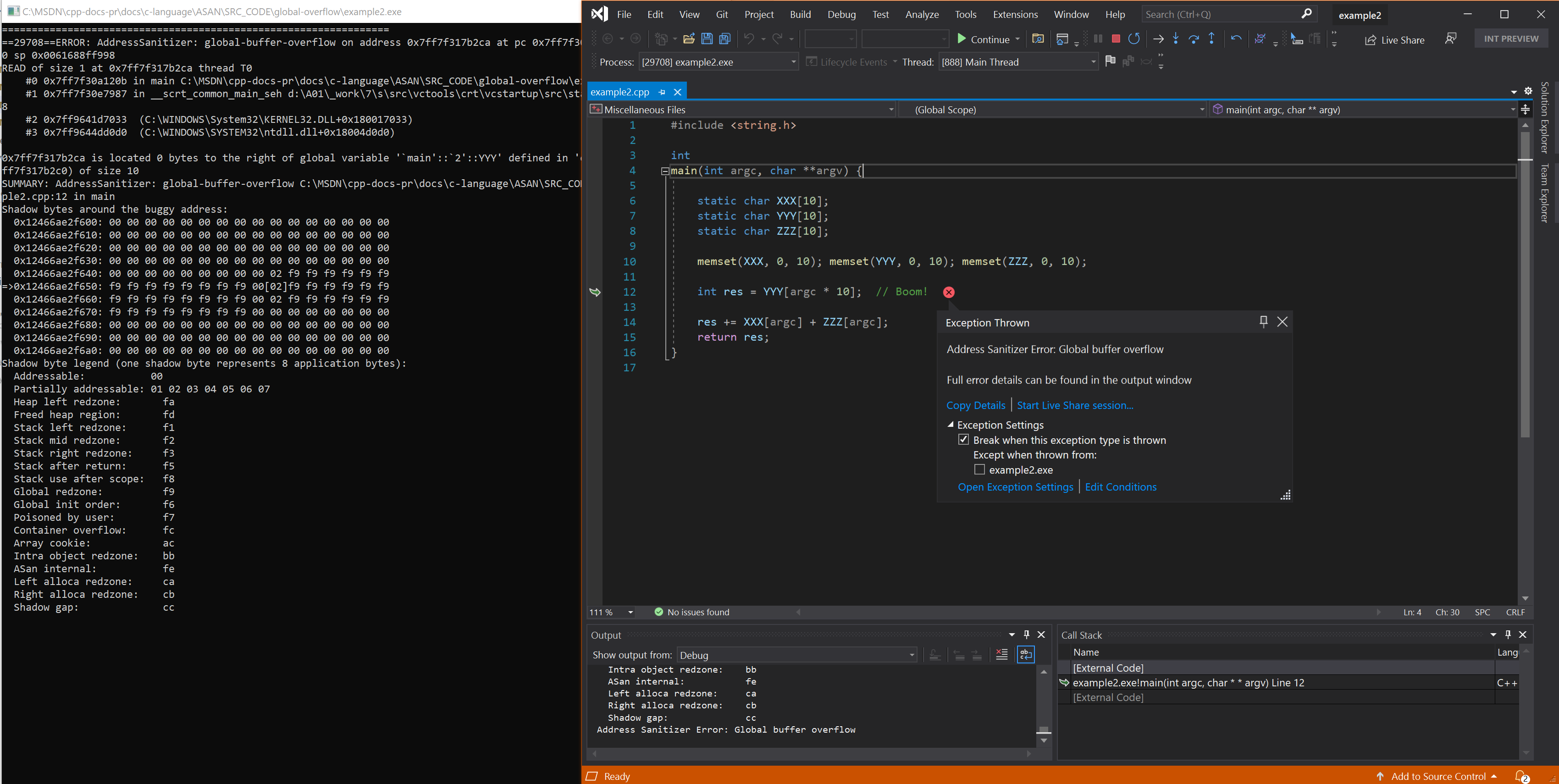
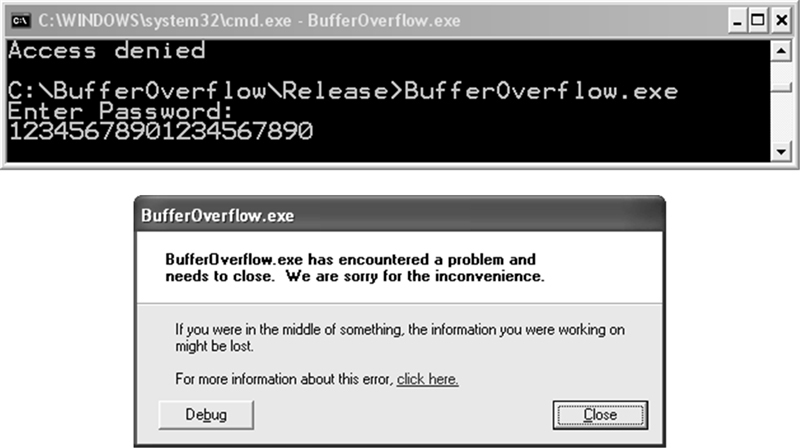
Buffer overflows What are buffer overflows? Basic stack exploit Some unsafe C lib functions Exploiting buffer overflows
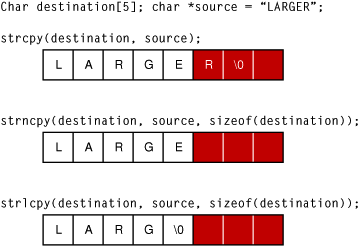
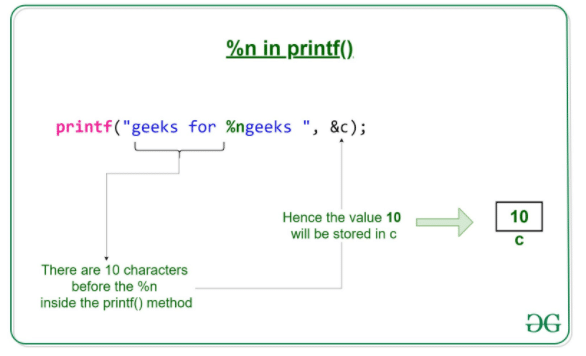
2.3. String Vulnerabilities and Exploits | Secure Coding in C and C++: Strings and Buffer Overflows | InformIT

Long string overflow the container of layout on events landing page · Issue #7 · govCMS/govCMS8-UI · GitHub
![PDF] Mutation-based testing of buffer overflows, SQL injections, and format string bugs | Semantic Scholar PDF] Mutation-based testing of buffer overflows, SQL injections, and format string bugs | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f49120b3a6e61a662d8ad339731525c0614458c9/20-Table2.2-1.png)




![java - String vs char[] - Stack Overflow java - String vs char[] - Stack Overflow](https://i.stack.imgur.com/WhEBr.png)